![[BKEYWORD-0-3] The Threat Of Cyber Security](http://www.haititechnews.com/wp-content/uploads/2014/08/cyber_security.jpg)
The Threat Of Cyber Security - that necessary
Who does not shop online in this day and age to purchase products and services? Who does not want to be able to choose from a myriad of options, compare shapes, sizes, colours, and prices, all from the convenience of the home without having to physically go to a store? Add to that the accessibility to products globally! Well, I believe, almost everyone does online shopping today, and numbers are increasing each day! The Covid pandemic drove people to start purchasing everyday goods online and forced even non-online shoppers to move to online shopping. So, what do eCommerce companies need to do to stay current, competitive, attract new customers, and provide their customers with a seamless and satisfying shopping experience? As the entire eCommerce business is digital and online, the primary source of threats to the companies is cyber-attacks. To understand what kinds of information security measures eCommerce companies should adopt, let us first look at few of the common and harmful cyber threats plaguing these businesses.Consider, what: The Threat Of Cyber Security
| The Threat Of Cyber Security | 889 |
| The Threat Of Cyber Security | 4 days ago · Dakota Murphey examines some of the most prominent cyber security threats to businesses and their employees throughout As if businesses didn’t have enough challenges to . Feb 01, · Threats beyond an organization’s control will continue to exist regardless of any action taken. When it comes to our society cyber-attacks can harm critical infrastructures like power supply, financial or communication services or our national defence systems. So, cybersecurity . 4 days ago · Dakota Murphey examines some of the most prominent cyber security threats to businesses and their employees throughout As if businesses didn’t have enough challenges to . |
| ANALYZING MOTIVES OF THE SOUTH AND THE | Gulf War Syndrome |
| An Analysis of Cantús Canícula Snapshots of | The Agency theory arises when business unit |
Microsoft is committed to protecting our customers and safeguarding our communities and we are proud to partner with industry partners to respond to this attack and strengthen our collective defenses.
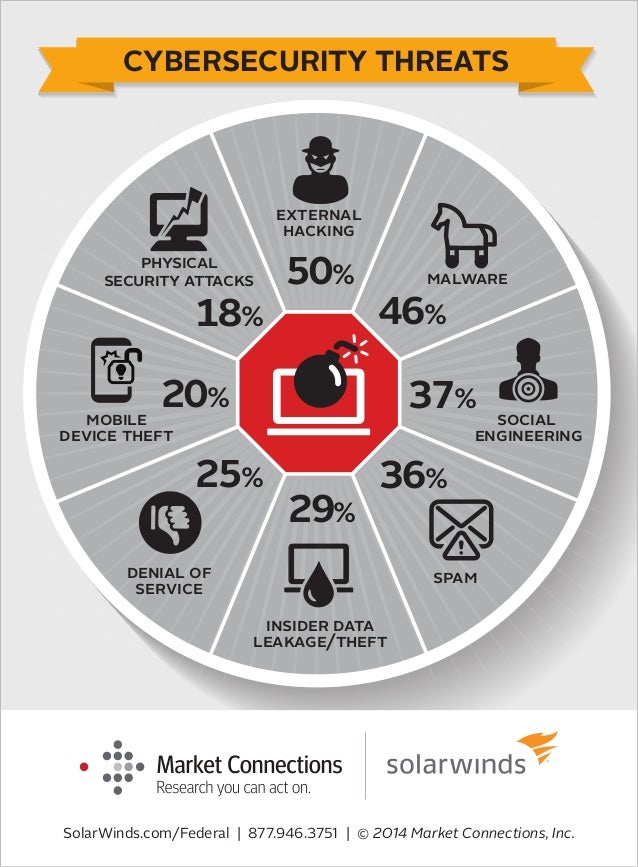
CYBER SECURITY THREATS TO E-COMMERCE
We believe transparency and clarity are important for strong cybersecurity and in that spirit, we are sharing information about some commonly asked questions. We look forward to serving and protecting our customers and communities. As Brad Smith wrote on December 17,Solorigate is a moment of reckoning for security.

We believe the Solorigate incident is an opportunity for the industry to work together to share information, strengthen defenses, and respond to attacks. We are proud to be part of the collaborative work being done to empower the defender community. Over the past two months, there have been several disclosures related to the Link actor and Microsoft has had a unique perspective from several angles:.

In all of our investigations to date, data hosted in Microsoft services including email was sometimes a target in the incidents, but the attacker had gained privileged credentials in some other way. Find the latest findings and guidance on Solorigate here.
INTEGRAL REQUIREMENTS OF AN E-COMMERCE BUSINESS
How do you respond? We have a very talented and experienced cybersecurity response team. In those situations where we provide investigative support to other organizations, we are restricted from sharing details. In these engagements, as well as when we notify organizations, those organizations have control in deciding what details they disclose and when they disclose them. Additionally, investigations sometimes discover early indicators that require further research before they are actionable.
Post navigation
Taking the time to thoroughly investigate incidents is necessary in order to provide the best guidance to the broader security community, our customers, and our partners. We share actionable information regularly on our Solorigate Cybeg centerand we are committed to providing additional updates if and when we discover new information to help source and enable the community. Has Microsoft in any way been an initial entry point for the Solorigate actor?
In our investigations to date, data hosted in Microsoft services including email was sometimes a target in the incidents, but the attacker had gained privileged credentials in some other way. From the beginning, we have said that we believe this is a sophisticated Tye that has many tools in its toolkit, so it is not a surprise that a sophisticated actor would also use other methods to click access to targets.]
Excuse, that I interrupt you, but, in my opinion, this theme is not so actual.
It is a lie.