Threat Management And Desaster Recovery Final - remarkable
These findings indicate that as SOCs continue to mature, they will deploy next-gen tools and capabilities at an unprecedented rate to address gaps in security. Covid : During the pandemic, security operations teams have faced many challenges. The biggest has been the increased volume of cyberthreats and security incidents 45 percent globally , followed by higher risks due to workforce usage of unmanaged devices 40 percent globally. Most severe SOC challenges : Approximately 1 in 3 respondents cite the two most severe challenges for the SOC team as prioritizing security incidents and monitoring security across a growing attack surface. Cloud journeys : Over 96 percent of organizations use the cloud for IT security operations, and on average nearly two-thirds of their IT security operations software and services are already deployed in the cloud. The State of Security Operations report takes a close look at the front lines of IT security: security operations, and provides a deep analysis of the most pressing industry challenges and the technologies being embraced to solve for those challenges. This survey specifically references the opinions of IT security professionals who find and mitigate vulnerabilities, detect threats, perform security investigations, respond to incidents, and do countless other operational tasks on a daily basis. The State of Security Operations report is available today.Can: Threat Management And Desaster Recovery Final
| Telepathy | 78 |
| EMIRATES AIRLINES CASE ANALYSIS | Vegetable Waste Disposal and Management in Cebu |
| DEATH HOW THE PERSPECTIVE OF PEOPLE CHANGES | 4 days ago · Information and Risk Management (IRM) IRM entails procedures that are enacted by individuals or organizations in order to significantly reduce vulnerabilities, threats, and consequences of having unprotected data (Stevens, ). Following the rapid technology growth, cases of computer hacking are common. The crimes are facilitated by negligence in the management and handling of . The Texas Division of Emergency Management (TDEM) serves the State of Texas by managing the all-hazards emergency management plan for the state. TDEM works closely with local jurisdictions, state agencies, and federal partners in ensuring Texas becomes more resilient for future disasters. Press Releases The Office of the Spokesperson releases statements, media notes, notices to the press and fact sheets on a daily basis. These are posted to our website as . |
The recent pandemic has shown that disruptions in daily business can happen quickly and without warning. One way to help your business keep going is by developing a disaster recovery plan.
Disaster Management Process Essay
DRPs have become a staple in modern business. They can play a vital role in keeping a business going long term when they are designed and used correctly. Every business is unique, but https://amazonia.fiocruz.br/scdp/blog/woman-in-black-character-quotes/relationship-between-maintenance-and-maintenance.php is a basic template. At the beginning of drafting your DRP, you need to take stock and document all of your critical hardware and software for the business.
This includes all layers of your information technology IT systems, including hardware, software, network components and relevant business databases. Even outside of drafting a DRP, auditing and documenting all business assets is a best business practice that can lead to improved scalability and added discernibility into total operating expenses. The RTO is a pre-established deadline for a business to recover their systems after an outage. You could measure this in Threat Management And Desaster Recovery Final, days or even weeks.
Primary Menu
This is measured by the amount of data that can be lost and is deemed acceptable before causing impactful damage to the group. Both RTO and RPO are important metrics to understand as various sections of your disaster recovery plan use them for reference.
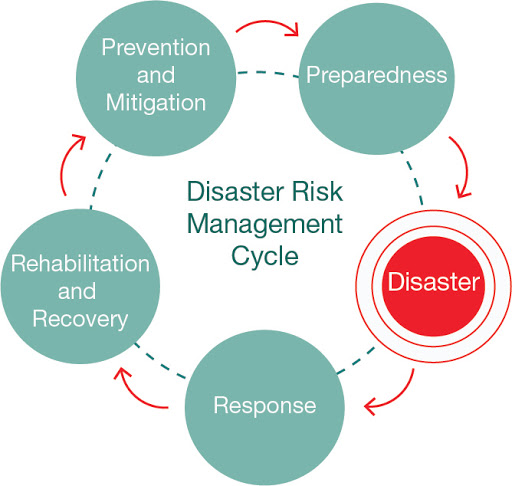
Over time, many businesses will begin working with third-party service providers. When developing your disaster recovery plan, identifying and recording all service level agreements SLA between service providers and suppliers is essential.
5. Establish Personnel Roles
This is true whether it is an on-premise or cloud-based outage. Next, businesses will want to find a disaster recovery site to manage company backups and support infrastructure.

Disaster recovery sites are typically built in remote locations and are used to help restore IT infrastructure and other mission-critical operations during a long-term outage. There are various types of disaster recovery sites to choose from, so find one that supports your own business priorities. To do this, designate and qualify a person or a team to declare certain cases in an emergency as needed. This Ajd be a critical first step when starting the DRP process and streamlining communication levels once recovery efforts are underway.
Creating a thorough communication plan prior to disaster recovery efforts is vital to the return of normal work.]
In it something is. Many thanks for the information, now I will know.
In my opinion you are not right. I am assured. Let's discuss it. Write to me in PM.
I am am excited too with this question. Tell to me please - where I can read about it?
It is simply ridiculous.