Target s Data Breach And Aftermath How - assured
In January, we recorded 82 publicly disclosed security incidents, which accounted for million breached records. Healthcare data has always been an attractive target for cyber criminals, and it has become even more popular during the pandemic. The breached data includes home addresses, email addresses, telephone numbers, dates of birth and social security numbers. Dutch police launched an investigation and arrested two suspects within 24 hours. A third suspect was arrested this week. According to Verlaan, the attackers worked in government call centres, where they had access to national COVID systems and databases. Last month, police in Ireland investigate how several people gained unauthorised access to a video lesson at a County Meath school. The attack, which targeted second-year students, was particularly troubling as hackers engaged in inappropriate behaviour. Luke Irwin is a writer for IT Governance. Your email address will not be published. Target s Data Breach And Aftermath How![[BKEYWORD-0-3] Target s Data Breach And Aftermath How](http://image.slidesharecdn.com/target-webinar-final-deck-140331154131-phpapp02/95/data-breach-at-target-demystified-9-638.jpg?cb=1412344704)
In the legal profession, information is the key to success.
US Sections
Law provides the intelligence you need to remain an expert and beat the competition. Already a subscriber?

Click here to login. Enter your details below and select your area s of interest to stay ahead of the curve and receive Law's daily newsletters.
Global Sections
First Name. Last Name.
Password at least 8 characters required. Confirm Password. Law may contact you in your professional capacity with information about our other products, services and events that we believe may be of interest.
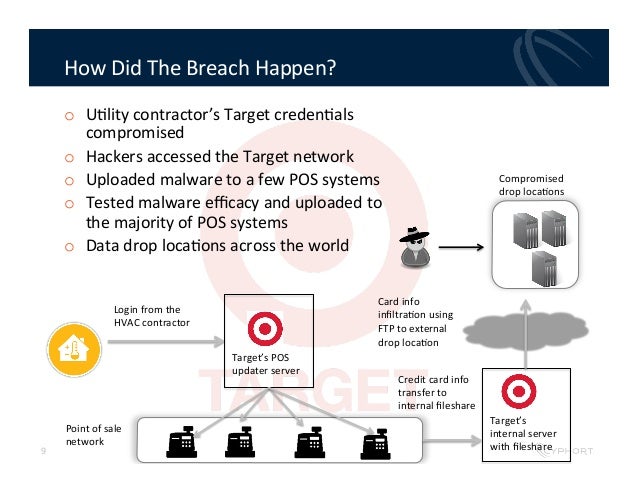
Step 1: Install Malware that Steals Credentials
We take your privacy seriously. Please see our Privacy Policy. Law takes your privacy seriously. District Judge Wilhelmina M. Stay ahead of the curve In the legal profession, information is the key to success. Access to case data within articles numbers, filings, courts, nature of suit, and more. Access to attached documents such as briefs, petitions, complaints, decisions, motions, etc.]
I am sorry, it not absolutely that is necessary for me.