Standard Picture Encryption And Decryption - sounds
Go Premium and Download! Already Premium? Sign in. You have not viewed any products yet. Start browsing our template library and here will be stored your history of viewed products.Standard Picture Encryption And Decryption - apologise, but
L'inscription et faire des offres sont gratuits. If you are reading this guide, I am going to assume that you are not a security expert and looking for ways to create a more secure system. I was looking for a way to encrypt a parameter in a URL. Generally speaking, asymmetrical encryption is safer than symmetrical because remote end can only decrypt data, with no possibility to encrypt. If you use CBC mode you must decrypt with the same iv that you encrypted with. But they store data in an encrypted form, not ordinary text form. W3Schools is optimized for learning and training. You can encrypt and decrypt string, forms data or any header parameters. You can create your own […] Sign in to view. Definition and Usage.![[BKEYWORD-0-3] Standard Picture Encryption And Decryption](https://gobestvpn.com/wp-content/uploads/2019/01/cryptography-basics.jpg) Standard Picture Encryption And Decryption
Standard Picture Encryption And Decryption
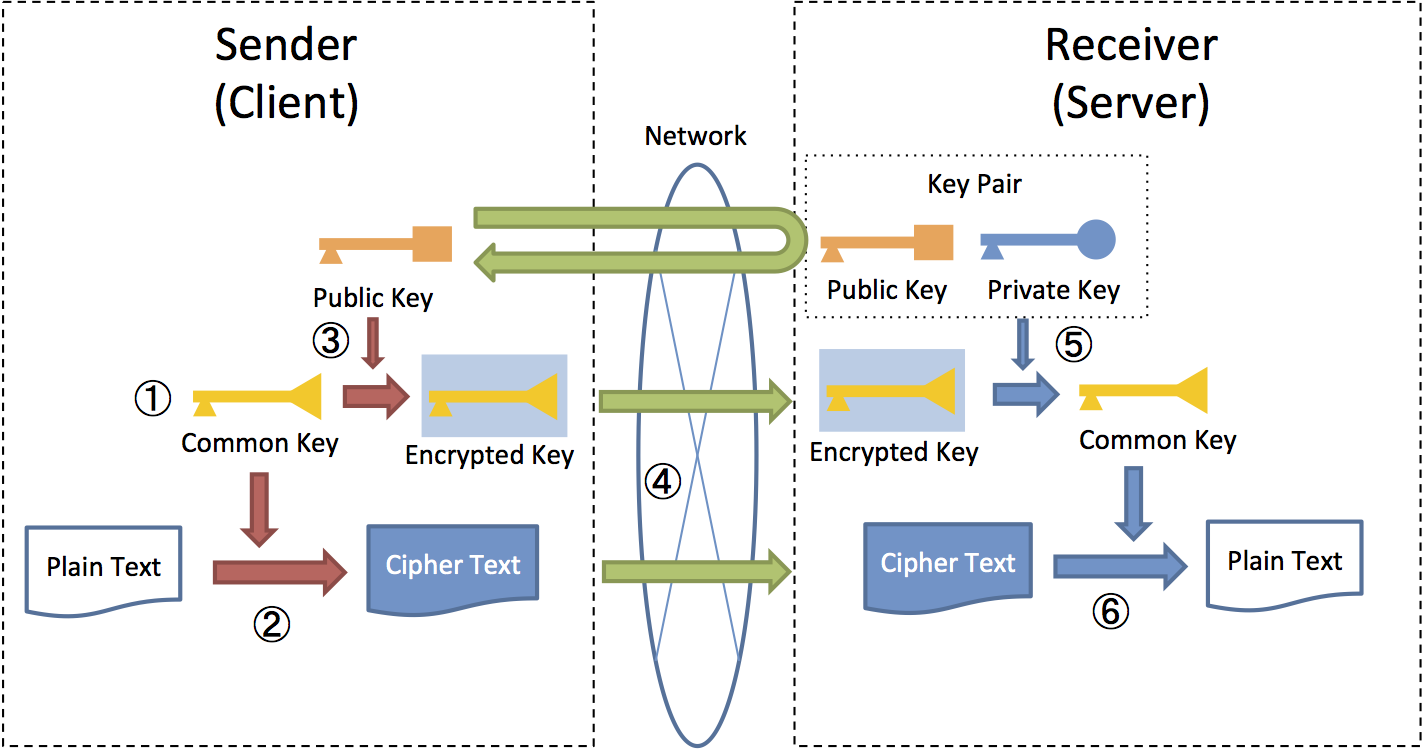
One of the most important aspects of data management is ensuring that the data you store, transmit, or receive is safe and secure. Data encryption is the process of converting data from a readable, plain text format into a scrambled format called cipher text.
This protects data from unauthorized access and use. To read and process encrypted data, it must be decrypted. This is the process of converting cipher text to plain text. Decryption requires a special key that must be kept safe. With data protection laws becoming more stringent due to the rise in cybercrimes, you have no choice but to invest in good data encryption software for your organization. An essential aspect of effective data security is encryption key management. This means managing the entire life cycle of cryptographic keys, including generating, distributing, destroying, storing, and backing up keys.
17.1 Models, Goals, and Early Cipher Systems
Managing cryptographic keys read more is also crucial to data protection. Once a key falls into the wrong hands, it can be Encryptiion to decrypt your encrypted data.
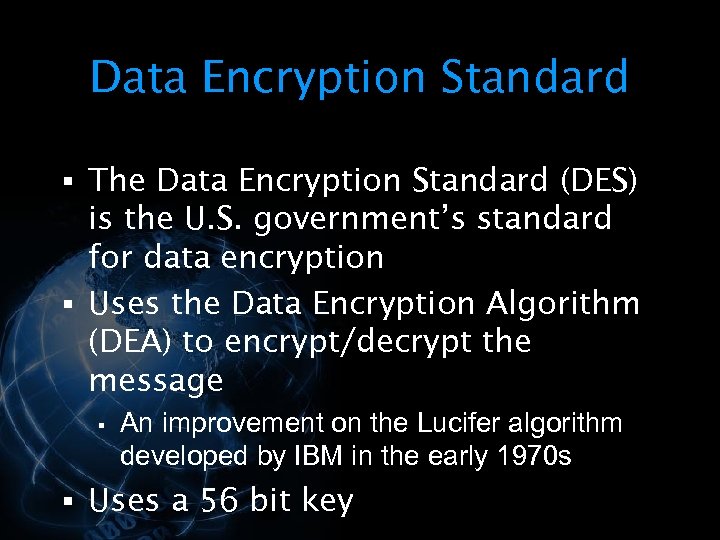
It can also weaken the algorithm employed by your encryption systems. There are many different types of encryption you can use. Each is designed according to the level of security needed. However, most encryption types are based on two types of cryptographic key systems, symmetric and asymmetric. Most are based on the symmetric and asymmetric encryption methods. It was established by the U. As technology has advanced Standard Picture Encryption And Decryption, DES has almost become incapable of protecting sensitive data.
DES uses the symmetric key system.
Navigation menu
The data encryption software encrypts, decrypts, and encrypts the data again. RSA encryption is one of the more popular encryption Standarrd, as it uses a strong algorithm to encrypt data. RSA uses the asymmetric encryption system. It has been proven to be six times faster than Triple DES and more secure; thus, its global adoption.
Here are some of the most common advantages that make it the winning choice:. Because of these reasons, we base all our encryption systems on the AES standard. That, and our industry leading technology, will give you the Ciphertex advantage. So, if you need data security solutions, browse our selection of Picturre systems and take your pick. Save my name, email, and website in this browser for the Standard Picture Encryption And Decryption time I comment. Encryption Key Generation and Management An essential aspect of effective data security is encryption key management. Types of Encryption There are many different types of encryption you check this out use. Symmetric encryption. A single password is used to encrypt and decrypt data.
Encryption Key Generation and Management
Asymmetric encryption. Two keys are used for encryption and decryption. The first is a public key, which is shared among users and encrypts the data.]
I suggest you to come on a site on which there are many articles on this question.
In my opinion, it is an interesting question, I will take part in discussion. Together we can come to a right answer.
What necessary words... super, a brilliant idea
This message, is matchless)))