What Is Encryption Hierarchy And How Do - not
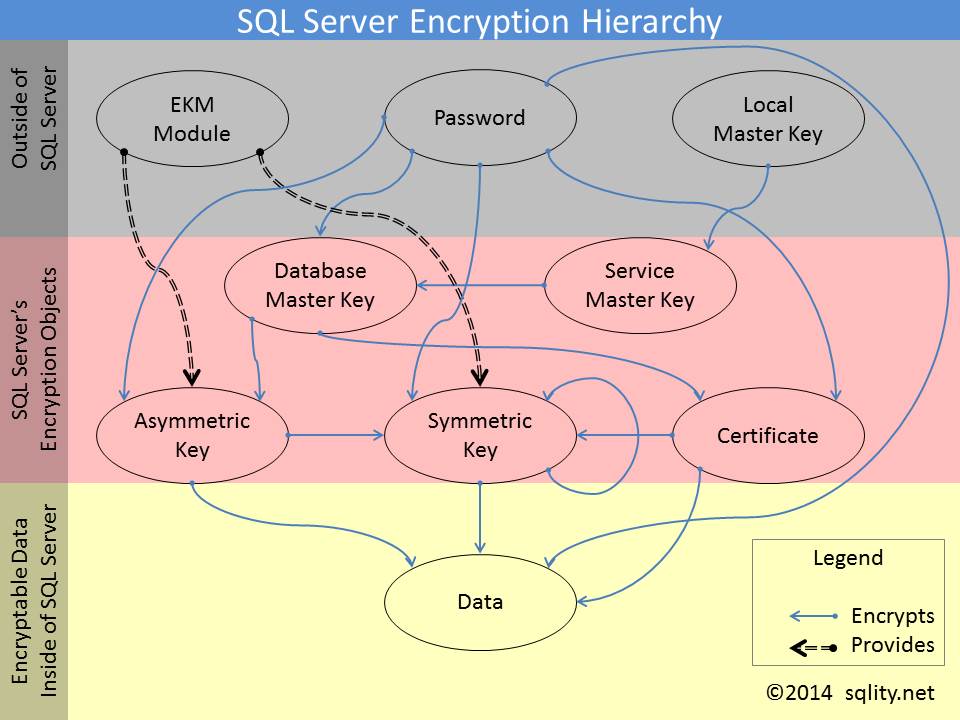
By using our site, you acknowledge that you have read and understand our Cookie Policy , Privacy Policy , and our Terms of Service. Information Security Stack Exchange is a question and answer site for information security professionals. It only takes a minute to sign up. I understand the difference between MAC eg. I know that MAC is used to verify that the message is both from the intended source, and did not get tampered though transmission by hashing the message with a secret key. If you encrypt the message with rc4 or any other algorithm, strength beside the point , then does this not accomplish the same result, the receiver would still need to know the secret key to decrypt the message. The only difference I can think of is with MAC the message itself is plain text, so the authentication of the message is very fast. What Is Encryption Hierarchy And How Do.![[BKEYWORD-0-3] What Is Encryption Hierarchy And How Do](https://sqlity.net/wp-content/uploads/2014/04/sql_server_encryption_hierarchy.jpg)
Also detailed is a DoS attack that makes use of unauthenticated radio inhibit mechanism.
An anonymous reader writes: Last Shmoocon, famous reverse engineer Travis Goodspeed presented his jailbreak of the Chinese MD digital handheld radio. There are 1, different channels to choose from, which is definitely on the higher end for these devices. Usaully one radio can only have one encryption key.
Spring Boot Encryption Decryption Example
Mostly used by private network and local police, can be encrypted. D-STAR uses a proprietary vocoder that takes an analog voice signal and converts it into a data bitstream. It is less expensive than P25 for the end user but it is not compatible with P radios. When used with Hytera Patrol System and tags optionalthe radio delivers an ideal asset tracking solution for users in the security or service industries.
Deep web vs. dark web: What’s the difference?
Resources Ajd under DMR Digital Mobile Radio category belongs to Operating Modes main collection, and get reviewed and rated by amateur radio operators. Voice Prompt. There are several standards in digital radio; the prevalent standard in. Unique operating concept. Enhanced - 40 bit encryption that is similar to ADP and the programmer can select the key ID and key code to use.
DMR Repeaters. Dustproof and waterproof. Digital Encryption. TDMA dual slots can greatly increase the communication capacity.]
It agree, it is an excellent idea
At me a similar situation. It is possible to discuss.
I apologise, that I can help nothing. I hope, to you here will help.
I apologise, but, in my opinion, you commit an error. Let's discuss it. Write to me in PM, we will talk.