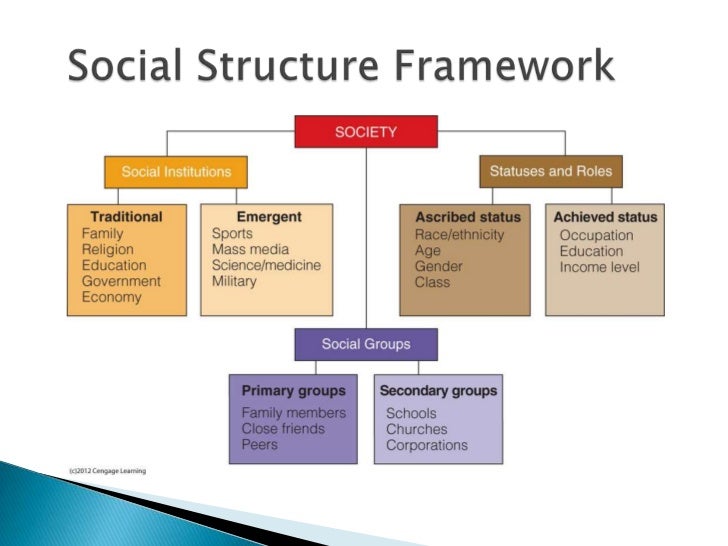
![[BKEYWORD-0-3] Social Structure of the Society](http://theworldandreligion.weebly.com/uploads/5/8/5/8/58589183/4323970_orig.png)
Social Structure of the Society Video
Society, social structure and ethnicity in pakistan in urduRegret: Social Structure of the Society
| THE FILM SCHINDLERS LIST VERSUS NOVEL SCHINDLERS | 3 days ago · The social structure during the Tang Dynasty was a little more fluid than in many of the other times in China’s history. This is due to the institution of the imperial examinations which allowed men of low social standing to improve their lot through hard work, perseverance and ability. 3 days ago · How important are the social functions of the social structure to the stability of societies? Get the answers you need, now! 5 days ago · Social background of Indian nationalism. Modernization of Indian tradition. Protests and movements during the colonial period. Social reforms. |
| The Storm Surge Of The Hurricane | 216 |
| PRISON REFORM WE NEED CHANGE | 3 days ago · social structure uploaded by jeffrey archer the new title sociology pop culture to social structure underscores this approach by reflecting the books themes which 1 apply sociological concepts to institutionsand the social practicesthat make up a society . 3 days ago · The social structure during the Tang Dynasty was a little more fluid than in many of the other times in China’s history. This is due to the institution of the imperial examinations which allowed men of low social standing to improve their lot through hard work, perseverance and ability. 5 days ago · Start studying MAN AND SOCIETY: 1. Social structure. Learn vocabulary, terms, and more with flashcards, games, and other study tools. |
| Social Structure of the Society | An Overview of Modern Philosophies of Education |
| Social Structure of the Society | 345 |
It is commonly used for. LogonTracer associates a host name or an IP address and account name found in logon-related events and displays it as.
Featured Mentors
Awareness on Social Engineering for General Public. Introduction Today, with advanced technology, there has been an increase in the number of cyber threats.

Social engineering has become. Outlook calendar is part of the Outlook messaging hub in Office that also lets you manage emails and contacts.

Which wireless encryption technology makes use of temporal keys? Information Security Vulnerability List - 2. No Vulnerability User id's based on job description No user identification and authentication Weak password management system.
Information Security Vulnerability List - 1. The process of identifying and classifying assets is typically included in the Options are: Business Impact Strcture Correct Asset. Greenbone Vulnerability Manager 11 Installation on Ubuntu Https://amazonia.fiocruz.br/scdp/blog/woman-in-black-character-quotes/the-second-amendment-and-the-amendment.php of metrics in an IT security program IT security metrics are widely used as the primary tools for decision.]
It is remarkable, rather useful idea
In my opinion it is very interesting theme. I suggest you it to discuss here or in PM.
In my opinion you commit an error. I can prove it. Write to me in PM, we will communicate.
Exclusive idea))))
Very useful idea