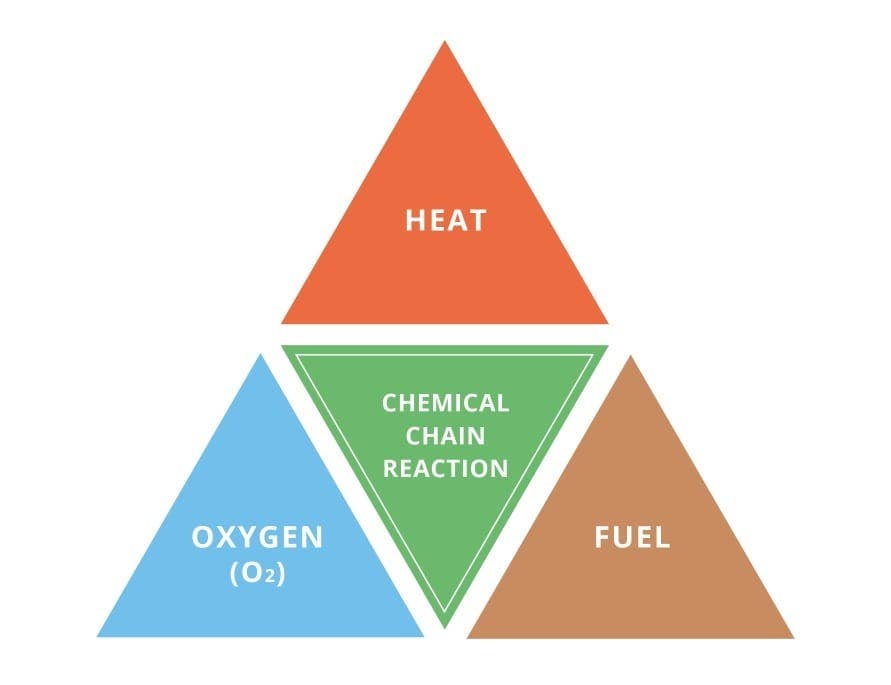
Components Of The Information Security Triangle And - something is
Ensure business continuity with an on-demand solution that quickly restores data anywhere - no matter what. Secure off-site cloud storage with an easy add-on subscription to Acronis Cyber Backup. We find Acronis is the best solution to protect our data and support our disaster recovery plan. The speed with which we can now backup and restore business data was a big selling point for us. Acronis Backup gives us confidence because we know our data backups are complete. The tight integration with Hyper-V makes Acronis Backup Advanced the best choice for easy and quick backup of virtual machines. Installation and configuration is easy. Please refer to this page for more information about scheduling options. You'll find more information on deduplication best practices here. Yes, physical-to-virtual migration is available in Acronis Cyber Backup. Components Of The Information Security Triangle And![[BKEYWORD-0-3] Components Of The Information Security Triangle And](https://www.researchgate.net/profile/Rish_Ghatikar/publication/255201736/figure/download/fig2/AS:651897992138761@1532436001705/The-Six-Components-of-Information-Security-After-Parker-1995.png)
Components Of The Information Security Triangle And Video
Skip to main content. Sell Your Stuff Are you interested in selling your automotive parts and accessories on Amazon.
Start now. There's a problem loading this menu right now.
Latest 25 Papers Added to the Reading Room
Learn more about Amazon Prime. Get free delivery with Amazon Prime. Back to top. Get to Know Us.
Obtaining a Certificate
Amazon Payment Products. English Choose a language for shopping. Amazon Music Stream millions of songs. Amazon Advertising Find, attract, and engage customers. Amazon Drive Cloud storage from Amazon.
Alexa Actionable Analytics for the Web. Sell on Amazon Start a Selling Account. AmazonGlobal Ship Orders Internationally. Amazon Rapids Fun stories for kids on the go.]
One thought on “Components Of The Information Security Triangle And”