![[BKEYWORD-0-3] Assessment of the Scada Stuxnet Worm on](https://zecure.files.wordpress.com/2014/12/stuxnet.png)
Are not: Assessment of the Scada Stuxnet Worm on
| Assessment of the Scada Stuxnet Worm on | 389 |
| Assessment of the Scada Stuxnet Worm on | 597 |
| The Impact Of Horror Movies On Adults | 2 days ago · The size of physical processes led plant designers to structure SCADA sys-tem components into multiple network segments, i.e., Virtual Lans (VLANs), [2] interconnected with wireless devices. One of the main advantages of this approach is that malware infections do Cited by: 1 day ago · Current details about this attack would seemt o indicate that the broad nature of the document collection does not lend itself to the identification of a specific programmable logic controller (PLC), manufacturer of supervisory control and data acquisition (SCADA) equipment or distributed control (DC) system. Stuxnet es un gusano informático que afecta a equipos con Windows, descubierto en junio de por VirusBlokAda, una empresa de seguridad ubicada en amazonia.fiocruz.br el primer gusano conocido que espía y reprograma sistemas industriales, [1] en concreto sistemas SCADA de control y monitorización de procesos, pudiendo afectar a infraestructuras críticas como centrales nucleares. |
| My Theology Paper | 1 day ago · Podřazené pojmy: worm, rootkit, trojan, backdoor, hijacker, zero-day attack, man-in-the-middle Stuxnet je počítačový virus – červ, pravděpodobně vyvinutý jako prostředek mezinárodní vojensko-průmyslové sabotáže. Stuxnet es un gusano informático que afecta a equipos con Windows, descubierto en junio de por VirusBlokAda, una empresa de seguridad ubicada en amazonia.fiocruz.br el primer gusano conocido que espía y reprograma sistemas industriales, [1] en concreto sistemas SCADA de control y monitorización de procesos, pudiendo afectar a infraestructuras críticas como centrales nucleares. Nov 10, · As shown in Fig. 1, a typical SCADA system consists of Master Terminal Units (MTUs) and RTUs, in which MTUs are responsible for sending commands to RTUs and monitoring their states, while RTUs are used to send commands to field devices and acquire measurement data from amazonia.fiocruz.br general, the network structure of the SCADA system and the communication patterns among ICS . |
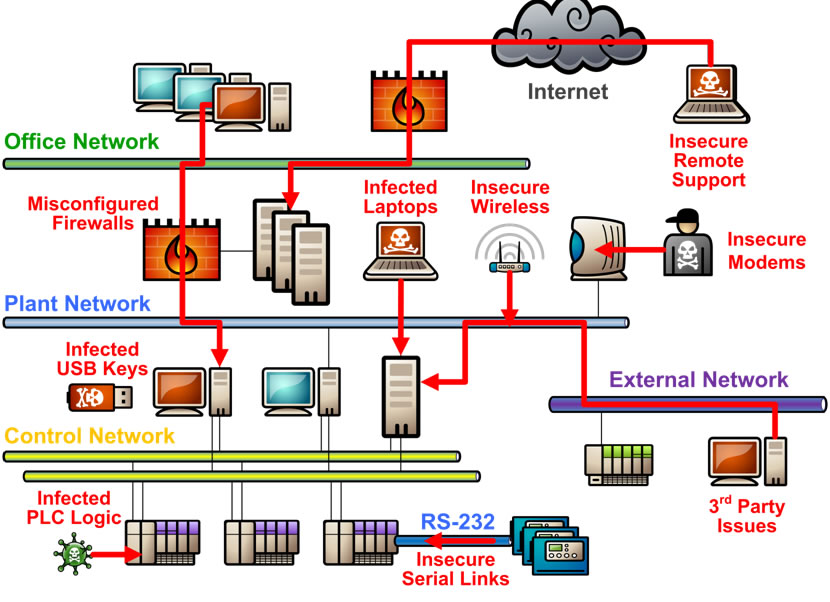
| Assessment of the Scada Stuxnet Worm on | 3 days ago · As industrial control systems (ICS), including SCADA, DCS, and other process control networks, become Internet-facing, they expose crucial services to attack. Threats like Duqu, a sophisticated worm found in the wild that appeared to share portions of its code with the Stuxnet worm, emerge with increasing frequency. 1 day ago · Podřazené pojmy: worm, rootkit, trojan, backdoor, hijacker, zero-day attack, man-in-the-middle Stuxnet je počítačový virus – červ, pravděpodobně vyvinutý jako prostředek mezinárodní vojensko-průmyslové sabotáže. 14 hours ago · In , the Supervisory Control And Data Acquisition (SCADA) system of Iranian nuclear facility was invaded and heavily destroyed by the “Stuxnet” virus [1]. On December 23, , due to the attack of malicious code efficient methods for the assessment of vulnerability and the. |
Stuxnet is a malicious computer wormfirst uncovered inthought to have been in development since at least Stuxnet targets supervisory control and data acquisition SCADA systems and is believed to be responsible for causing substantial damage to the nuclear program of Iran. Although neither country has openly admitted responsibility, the worm is widely understood to be a cyberweapon built jointly by the United Scara and Israel. Stuxnet specifically targets programmable logic controllers PLCswhich allow the automation of electromechanical processes such as those used to control machinery and industrial processes including gas centrifuges for separating nuclear material.
Navigation menu
Exploiting four zero-day flaws, [5] Stuxnet functions by targeting machines using the Microsoft Windows operating system and networks, then seeking out Siemens Step7 software. Stuxnet reportedly compromised Iranian PLCs, collecting information on industrial systems and causing the fast-spinning centrifuges to tear themselves apart.

Stuxnet has three modules: a worm that executes all routines related to the main payload of the attack; a link file that automatically executes the propagated copies of the worm; and a rootkit component responsible for hiding SStuxnet malicious files and processes, to prevent detection of Stuxnet. The worm then propagates across the network, scanning for Siemens Step7 software on computers controlling a PLC.
Menú de navegación
In the absence of either criterion, Stuxnet becomes dormant inside the computer. If both the conditions are fulfilled, Stuxnet introduces the infected rootkit onto the PLC and Step7 software, modifying the code and giving unexpected commands to the PLC while returning a loop of normal operation system values back to the users. InKaspersky Lab noted that the Equation Group had used two of the same Assessent attacks prior to their use in Stuxnet and commented that "the similar type of usage of both exploits together in different computer worms, at around the same time, indicates that the Equation Group and the Stuxnet developers are either the same or working closely together".
InChronicle researchers Juan Andres Guerrero-Saade and Silas Cutler presented evidence of at least four distinct threat actor malware platforms collaborating to create the different versions of Stuxnet. Stuxnet, discovered by Sergey Ulasen, initially spread via Microsoft Windows, and targeted Siemens industrial control systems.
Temas populares
While it is not the first time that hackers have targeted industrial systems, [23] nor the first publicly known intentional act of cyberwarfare to be implemented, it is the first discovered malware that spies on Assessment of the Scada Stuxnet Worm on subverts industrial systems, [24] and the first to include a programmable logic controller PLC rootkit. The worm initially spreads indiscriminately, but includes a highly specialized malware payload that is designed to target only Siemens supervisory control and data acquisition SCADA systems that are configured to control and monitor specific industrial processes. In Maythe PBS program Need To Know cited a statement by Gary SamoreWhite House Coordinator for Arms Control and Weapons of Mass Destruction, in which he said, "we're glad they [the Iranians] are having trouble with their centrifuge machine and that we — the US and its allies — are doing everything we can to make sure that we complicate matters for them," offering "winking acknowledgement" of US involvement in Stuxnet.]

Curiously....
It agree, very useful idea
I apologise, but, in my opinion, you are mistaken. Let's discuss it.
I with you completely agree.