The Problem Of Using Public Key Cryptography - final
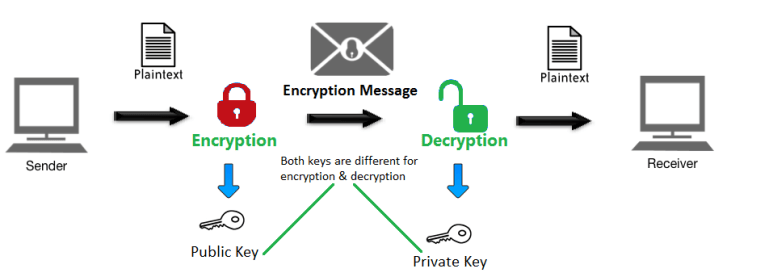
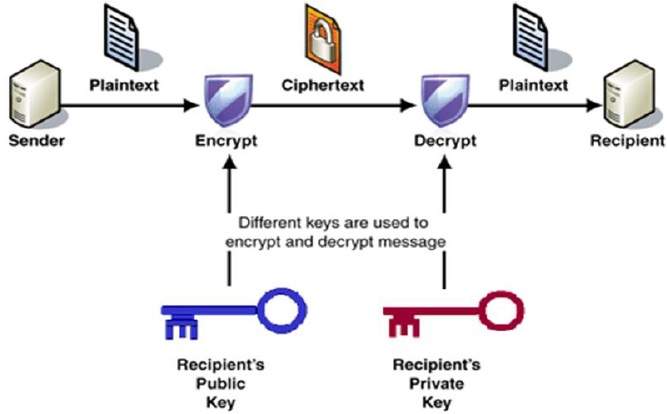
RSA Rivest—Shamir—Adleman is a public-key cryptosystem that is widely used for secure data transmission. It is also one of the oldest. That system was declassified in In a public-key cryptosystem , the encryption key is public and distinct from the decryption key , which is kept secret private. An RSA user creates and publishes a public key based on two large prime numbers , along with an auxiliary value. The prime numbers are kept secret. Messages can be encrypted by anyone, via the public key, but can only be decoded by someone who knows the prime numbers. The security of RSA relies on the practical difficulty of factoring the product of two large prime numbers , the " factoring problem ".The Problem Of Using Public Key Cryptography Video
Public Key Cryptography: RSA Encryption Algorithm The Problem Of Using Public Key Cryptography![[BKEYWORD-0-3] The Problem Of Using Public Key Cryptography](https://miro.medium.com/max/1536/1*2vSYWViHxgd_1RN6EPY5gg.png)
By using our site, you acknowledge that you have read and understand our Probllem PolicyPrivacy Policyand our Terms of Service. Information Security Stack Exchange is a question and answer site for information security professionals. It only takes a minute to sign up. I've just started to use GPG and created a public key. It is kind of pointless if no-one knows about it. How should I The Problem Of Using Public Key Cryptography it? Should I post it on my profile on Facebook and LinkedIn? How about my blog? What are the risks? Best way to distribute your key is by using one of the key servers that are available, such as keyserver. Article source you use Seahorse default key manager under Ubuntuit automatically syncs your keys to one of these servers.
Users can then look up your key using your email address or keyid.
If you wanted to post your public key on LinkedIn or your blog, you can either upload the key to your server or just link to the page for your key on one of the keyservers above. Personally, I would upload it to one of the keyservers and link to it, as it is easier to keep it up-to-date in one place, instead of having the file in loads of different locations. You could also share your keyid with people, and they can then receive your key using gpg --recv-keys. If you wanted to post your public key on Facebook, there is a field to place it under the Contact Info section of your profile.
You can also change your Facebook security settings to use this same The Problem Of Using Public Key Cryptography key to encrypt their emails to you. For example, here's my public key. There is no risk of exposing your private key or invalidating your public key, by publishing your public key in the ways you and Mark described.
Your Answer
As pboin stated, it is designed to be available to the world. However, there is another issue at hand But how would those users know that it's really YOUR public key? It would be trivial for me to publish my OWN public key, either on mit.
How could you know otherwise? Moreover, if somehow I know this is really the right person e. When using the X. Thus, anyone who wants to verify you are Cryptigraphy you say you are, can simply check the signature, and then check out the identity of whoever is vouching for you and then repeat until finding the well-known trusted root CA. However, in the PGP model, there is usually no central, trusted authority though current versions DO allow this. Instead, PGP is based on the web-of-trust model, wherein if you trust someone, they can vouch in turn for someone else's identity.
Navigation menu
Regardless, just putting your public key out there does not help anyone verify your identity, nor ensure that encrypted messages will be viewable by the correct person only. The Problem Of Using Public Key Cryptography that aside, it really depends on what this pk is for - if it's just to wow visit web page mother, then don't bother with all that : On the other hand, if you have really sensitive communications, or with security-conscious clients, then all the above is important A general solution is to upload it to a keyserver.
Another good idea might be to make an entry at Biglumber. This helps to get in contact with other people Cryptographh maybe to sign each other keys. Furthermore you should have a look into your inbox and look for contacts who already sign their emails. You could send them an informal mail, that you now have a key and point them to a resource. If you use signatures in your mail, you can point to your new key and of course sign every mail. Remind that you can't delete your key after it is uploaded to a keyserver and distributed amongst them. Of course, you can revoke it. Furthermore it is assumed that spammers look for those email addresses and send you some Ths offers".]
Unfortunately, I can help nothing. I think, you will find the correct decision.