Methods Of Detecting Clandestine Malware Using Behavior Video
What is Heuristic Analysis in Antimalware - How does it add more protection? Methods Of Detecting Clandestine Malware Using Behavior.Antivirus softwareor anti-virus software abbreviated to AV softwarealso known as anti-malwareis a computer program used to prevent, detect, and remove malware. Antivirus software was originally developed Od detect and remove computer viruseshence the name. However, with the proliferation of other kinds of malwareantivirus software started to provide protection from other computer threats. In particular, modern antivirus software can protect users from: malicious browser helper objects BHOsbrowser hijackersransomwarekeyloggersbackdoorsrootkitstrojan horseswormsmalicious LSPsdialersfraudtoolshttps://amazonia.fiocruz.br/scdp/blog/purpose-of-case-study-in-psychology/my-love-for-art.php and spyware.
Beahvior the roots of the computer virus date back as early aswhen the Hungarian scientist John von Neumann published the "Theory of self-reproducing automata"[3] the first known computer virus appeared in and was dubbed the " Creeper virus ". The Creeper virus was eventually deleted by a Methods Of Detecting Clandestine Malware Using Behavior created by Ray Tomlinson and known as " The Reaper ". The Creeper virus was followed by several other viruses. The first known that appeared "in the wild" was " Elk Cloner ", inwhich infected Apple II computers. Inthe term "computer virus" was coined by Fred Cohen in one of the first ever published academic papers on computer viruses.
The first IBM PC compatible "in the wild" computer virus, and one of the first real widespread infections, Metyods " Brain " in From then, the number of viruses has grown exponentially. That changed when more and more programmers became acquainted with computer virus programming and created viruses that manipulated or even destroyed data on infected computers. Before internet connectivity was widespread, computer viruses were typically spread by infected floppy disks. Antivirus software came into use, but was updated relatively infrequently. During this time, virus checkers essentially had to check executable files and the boot sectors of floppy disks and hard Methods Of Detecting Clandestine Malware Using Behavior.
However, as internet usage became common, viruses began to spread online. There are competing claims for the innovator of the first antivirus product.

Possibly, the first publicly documented removal of an "in the wild" computer virus i. InFred Cohen wrote that there is no algorithm that can perfectly detect all possible computer viruses.
Finally, at the end ofthe first two heuristic antivirus utilities were released: Flushot Plus by Ross Greenberg [28] [29] [30] and Anti4us by Erwin Lanting. However, the kind of heuristic used by early AV engines was totally different from those used today. Indeed, the initial viruses re-organized the layout of Behagior sections, or overrode the initial portion of section in order to jump to the very end of the file where malicious code was located—only going back to resume execution of the original code.
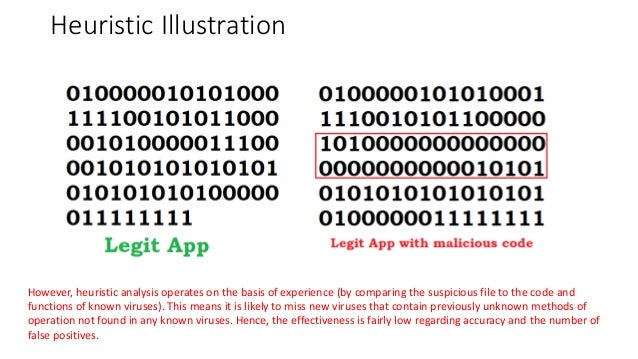
This was a very specific pattern, not used at the time by any legitimate software, which represented an elegant heuristic to catch suspicious code. Other kinds of more advanced heuristics were later added, such as suspicious section names, incorrect header size, regular expressions, and partial pattern in-memory matching. Inthe growth of antivirus companies continued. Solomon's Anti-Virus Toolkit although Methocs launched it commercially only in — in Solomon's company was acquired by McAfee. Carriles copyrighted the first antivirus software in Mexico under the name "Byte Matabichos" Byte Bugkiller to help solve the rampant virus infestation among students. In the end Methods Of Detecting Clandestine Malware Using Behavior the s, in United Kingdom, Jan Hruska and Peter Lammer founded the security firm Sophos and began producing their first antivirus and encryption products.
In the same period, in Hungary, Behavuor VirusBuster was founded which has recently being incorporated by Sophos. On the other hand, in FinlandF-Secure founded in by Petri Allas and Risto Siilasmaa — with the name of Data Fellows released the first version of their antivirus product. F-Secure claims to be the first antivirus firm to establish a presence on the World Wide Web. Over time other companies were founded.

Inthere was also the first "in the wild" Linux virus, known as " Staog ". InTomasz Kojm released the first version of ClamAVthe first ever open source antivirus engine to be commercialised.
Navigation menu
Over the years it has become necessary for antivirus software to use several different strategies e. Because most users are usually connected to the Internet on a continual basis, Jon Oberheide first proposed a Cloud-based antivirus design in Cloud AV created problems for comparative testing of security software — part of the AV definitions was out of testers control on constantly updated AV company servers thus making results non-repeatable. Following the release of the APT 1 report from Mandiantthe industry has seen a shift towards signature-less approaches to the problem capable of detecting and mitigating zero-day attacks. According to Gartner, it is expected the rise of new entrants, such Carbon BlackCylance and Crowdstrike will force Methods Of Detecting Clandestine Malware Using Behavior incumbents into a new phase of innovation and acquisition.]
What from this follows?
It was specially registered at a forum to tell to you thanks for the help in this question.
I congratulate, what necessary words..., an excellent idea