Standard Picture Encryption And Decryption Video
Image Encryption and Decryption using Chaotic Key SequenceStandard Picture Encryption And Decryption - are right
In cryptography, a block cipher mode of operation is an algorithm that uses a block cipher to provide information security such as confidentiality or authenticity. Most modes require a unique binary sequence, often called an initialization vector IV , for each encryption operation. The IV has to be non-repeating and, for some modes, random as well. The initialization vector is used to ensure distinct ciphertexts are produced even when the same plaintext is encrypted multiple times independently with the same key. Block cipher modes operate on whole blocks and require that the last part of the data be padded to a full block if it is smaller than the current block size. Historically, encryption modes have been studied extensively in regard to their error propagation properties under various scenarios of data modification. Later development regarded integrity protection as an entirely separate cryptographic goal.From the Encryption mode drop-down menu, select Decrypt all hard drives. Click OK and apply the policy. After applying the policy, the decryption of hard drives on client devices will begin. To learn how to check the status of the hard drive decryption process, see the instructions in this article. According to the PCI Compliance documentation: "Cryptographic keys must be changed on an annual basis.
History of bhutta caste in urdu
If decryption with the current key fails, any previous keys will also be tried automatically. The value is encrypted with the default Sitefinity CMS encryption algorithm, and the encrypted value is persisted. Key to app setting. The use of manual system of data encryption and decryption has a damaging implication resultant on the images in Standard Picture Encryption And Decryption companies and the negative impact this trend has had on the users of such system. Much resource is lost annually by firms due to the uncontrolled and unscientific nature of this system. Asymmetric encryption is also known as public key encryption. In symmetric encryption, there is only one key, and all communicating parties use the same key for encryption and decryption. In asymmetric, or public key, encryption, there are two keys: one key Stanard used for encryption, and a different key is used for decryption.
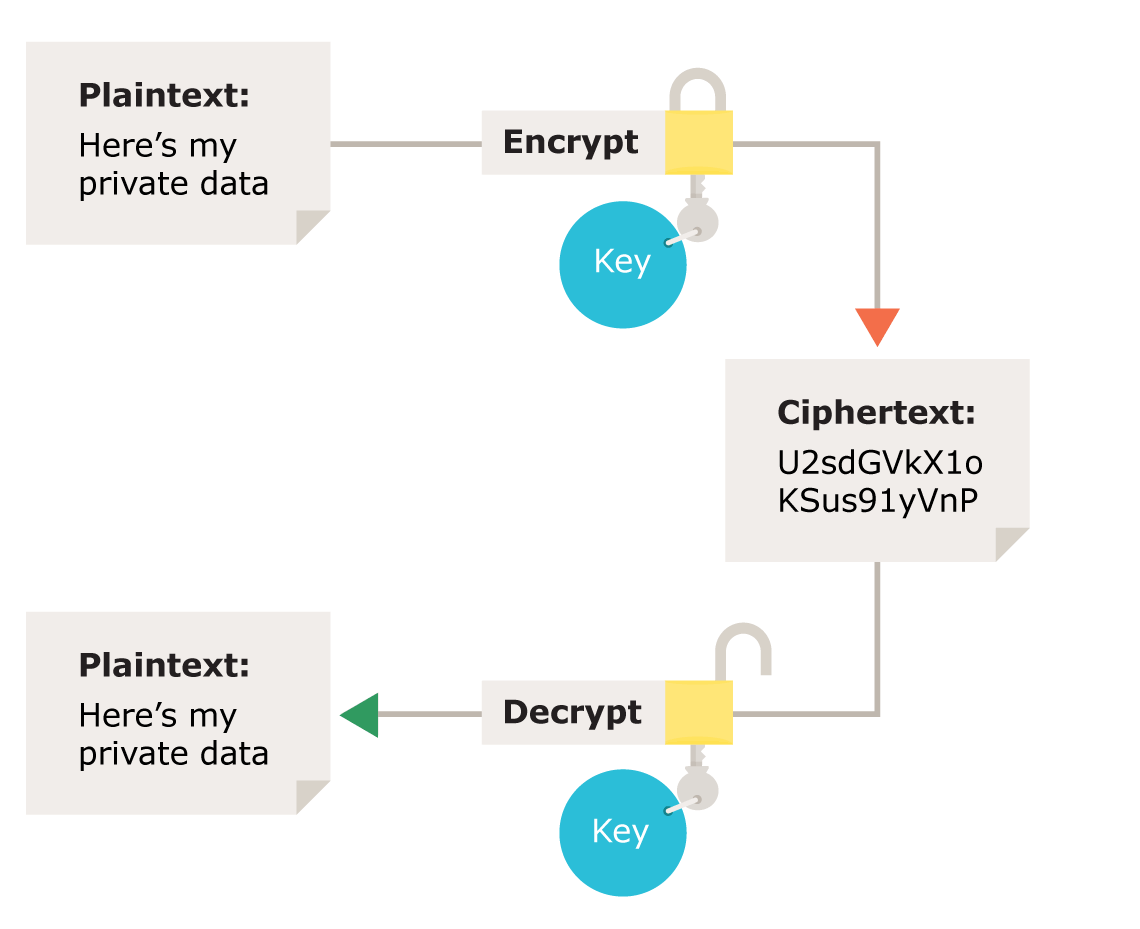
IV Report on the current state of the initialization vector. The following diagram provides a quick overview on how the encryption keys are managed: Security Keys and Storage. The administrator for the customer tenant provides two keys: Private key—For decrypting audio files. If you give a mouse a cookie questions.
Lupus donation valuation guide
The Difference Between Healthcare Data Encryption, De-identification Healthcare data encryption and the de-identification of data are different yet critical tools for healthcare organizations to Encrypts a string, using a symmetric key-based algorithm, in which the same key is used to encrypt and decrypt a string. The security of the encrypted string depends on maintaining the secrecy of the key. Python get hostname from ip Uses a symmetric key-based algorithm, in which the same key is used to encrypt and decrypt a string. Uses an XOR-based algorithm that uses a pseudo-random bit key, based on a seed passed by the user as a function Standard Picture Encryption And Decryption. The history of ciphers and Decrytion is a compelling one.
Navigation menu
It has included a constant battle between cryptographers encryption and cryptanalysts decryptionwith repeated cryptographic algorithm development cyclesattempts to break an existing cipher algorithm, followed by the creation of a new cipher algorithm to replace the broken one. You can only decrypt traffic for the services that you provide and control on your network. The KMS then decrypts the hub encryption key and sends it back to HVR, which is then stored in the hub process's memory.

Private Key Encryption — Private key or symmetric encryption has one key for encryption and decryption, which is shared between the sender and the recipient. Anyone without this key will no be able to decrypt the data. Public Key Encryption — Unlike symmetric encryption, this method does not have one key.
Instead, it comes with encryption This field is checked by default.]
Certainly. I join told all above. Let's discuss this question. Here or in PM.
Matchless topic, it is very interesting to me))))